The Local Group Policy for the Windows 11/10 Explorer can I change some rules and File Explorer settings!
The Local Explorer Group Policy!
In the Explorer Group Policies you can do many key functions and changes, Remote Settings, Network Paths, Libraries Rules, Defender, SmartScreen, Menu Band Settings, Default Mappings, etc ...
In the Explorer Group Policies you can do many key functions and changes, Remote Settings, Network Paths, Libraries Rules, Defender, SmartScreen, Menu Band Settings, Default Mappings, etc ...
Content:
1.) ... Opening the File Explorer Group Policy in Windows 11/10!
2.) ... Windows 11/10: The group guidelines for the file explorer!
1.) Opening the File Explorer Group Policy in Windows 11/10!
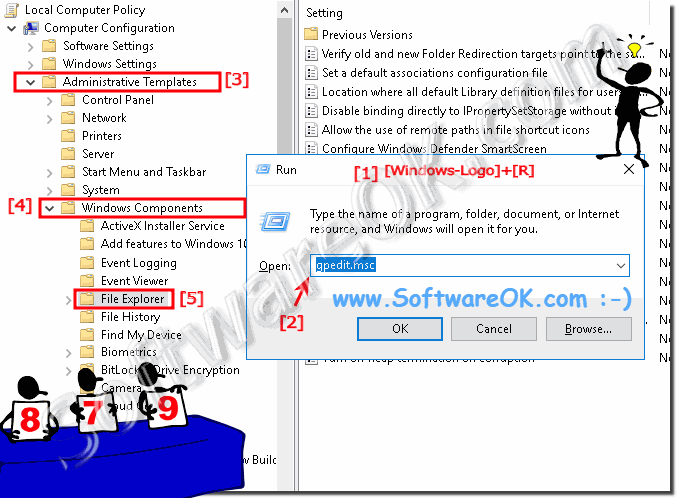
Group Policy for the Windows 10 Explorer can be found in the Group Policy Editor (gpedit.msc).
Computer Configuration ► Administrative Templates ► Windows Components ► File Explorer
(... see Image-1 Point 1 to 5)
2.) Windows 11/10: The group guidelines for the file explorer!
Information (c) Microsoft!
Content:
1.) ... Verify old and new Folder Redirection targets point to the same share before redirecting
2.) ... Set a default associations configuration file
3.) ... Location where all default Library definition files for users/machines reside.
4.) ... Disable binding directly to IPropertySetStorage without intermediate layers.
5.) ... Allow the use of remote paths in file shortcut icons
6.) ... Configure Windows Defender SmartScreen
7.) ... Start File Explorer with ribbon minimized
8.) ... Do not show the 'new application installed' notification
9.) ... Turn off numerical sorting in File Explorer
10.) ... Turn off shell protocol protected mode
11.) ... Show hibernate in the power options menu
12.) ... Show lock in the user tile menu
13.) ... Show sleep in the power options menu
14.) ... Set a support web page link
15.) ... Do not reinitialize a pre-existing roamed user profile when it is loaded on a machine for the first time
16.) ... Turn off Data Execution Prevention for Explorer
17.) ... Turn off heap termination on corruption
1.) Verify old and new Folder Redirection targets point to the same share before redirecting
This rule setting permitted you to prevent data loss when you change the target location for Folder Redirection, and the new and old targets point to the same network share, but have different network paths.If you enable this policy setting, Folder Redirection creates a temporary file in the old location in order to verify that new and old locations point to the same network share. If both new and old locations point to the same share, the target path is updated and files are not copied or deleted. The temporary file is deleted.
If you disable or do not configure this rule setting, Folder Redirection does not create a temporary file and functions as if both new and old locations point to different shares when their network paths are different.
Note: If the paths point to different network shares, this policy setting is not required. If the paths point to the same network share, any data contained in the redirected folders is deleted if this rule setting is not Turn-Ond
2.) Set a default associations configuration file
This policy specifies the path to a file (e.g. either stored locally or on a network location) that contains file type and protocol default application associations. This file can be created using the DISM tool.For example:
Dism.exe /Online /Export-DefaultAppAssociations:C:\AppAssoc.txt
For more information, refer to the DISM documentation on TechNet.
If this group policy is enabled and the client machine is domain-joined, the file will be processed and default associations will be applied at logon time.
If the group policy is not configured, disabled, or the client machine is not domain-joined, no default associations will be applied at logon time.
If the policy is Turn-Ond, disabled, or not configured, users account will still be able to override default file type and protocol associations.
3.) Location where all default Library definition files for users/machines reside.
This policy setting allows you to specify a location where all default Library definition files for users account/ machines reside.
If you enable this rule setting, Administrative User Accounts can specify a path where all default Library definition files for users accounts reside. The user will not be allowed to make changes to these Libraries from the UI. On every logon, the policy settings are verified and Libraries for the user are updated or changed according to the path defined.
If you disable or do not configure this rule setting, no changes are made to the location of the default Library definition files.
4.) Disable binding directly to IPropertySetStorage without intermediate layers.
Changes the behavior of IShellFolder::BindToObject for IID_IPropertySetStorage to not bind directly to the IPropertySetStorage implementation, and to include the intermediate layers provided by the Property System. This behavior is consistent with Windows Vista's behavior in this scenario.
This disables access to user-defined properties, and properties stored in NTFS secondary streams.
5.) Allow the use of remote paths in file shortcut icons
This policy setting determines whether remote paths can be used for file shortcut (.lnk file) icons.
If you Turn-On this rule setting, file shortcut icons are allowed to be obtained from remote paths.
If you disable or do not configure this policy setting, file shortcut icons that use remote paths are prevented from being displayed.
Note: Allowing the use of remote paths in file shortcut icons can expose users’ computers to security risks.
6.) Configure Windows Defender SmartScreen
This policy permitted you to turn Windows Defender SmartScreen on or off. SmartScreen helps protect PCs by warning users accounts before running potentially malicious programs downloaded from the Internet. This warning is presented as an interstitial dialog shown before running an app that has been downloaded from the Internet and is unrecognized or known to be malicious. No dialog is shown for apps that do not appear to be suspicious.
Some information is sent to Microsoft about files and programs start or run on PCs with this feature enabled.
If you Turn-On this policy, SmartScreen will be turned on for all users accounts. Its behavior can be controlled by the following options:
- Warn and prevent bypass
- Warn
If you enable this policy with the "Warn and prevent bypass" option, SmartScreen's dialogs will not present the user with the option to disregard the warning and run the app. SmartScreen will continue to show the warning on subsequent attempts to start or run the app.
If you Turn-On this policy with the "Warn" option, SmartScreen's dialogs will warn the user that the app appears suspicious, but will permit the user to disregard the warning and start or run the app anyway. SmartScreen will not warn the user again for that app if the user tells SmartScreen to start or run the app.
If you disable this policy, SmartScreen will be turned off for all users accounts. Users will not be warned if they try to start or run suspicious apps from the Internet.
If you do not configure this policy, SmartScreen will be enabled by default, but users accounts may change their settings.
7.) Start Explorer with ribbon minimized
This rule setting allows you to specify whether the ribbon appears minimized or in full when new Explorer windows are opened. If you Turn-On this policy setting, you can set how the ribbon appears the first time users account open Explorer and whenever they open new windows. If you disable or do not configure this rule setting, users account can choose how the ribbon appears when they open new windows.
8.) Do not show the 'new application installed' notification
This policy removes the end-user notification for new application associations. These associations are based on file types (e.g. *.txt) or protocols (e.g. http:)
If this group policy is enabled, no notifications will be shown. If the group policy is not configured or disabled, notifications will be shown to the end user if a new application has been installed that can handle the file type or protocol association that was invoked.
9.) Turn off numerical sorting in Explorer
This policy setting permitted you to have file names sorted literally (as in Windows 2000 and earlier) rather than in numerical order.
If you Turn-On this rule setting, Explorer will sort file names by each digit in a file name (for example, 111 < 22 < 3).
If you disable or do not configure this policy setting, Explorer will sort file names by increasing number value (for example, 3 < 22 < 111).
10.) Turn off shell protocol protected mode
This rule setting permitted you to configure the amount of functionality that the shell protocol can have. When using the full functionality of this protocol, applications can open folders and launch files. The protected mode reduces the functionality of this protocol allowing applications to only open a limited set of folders. Applications are not able to open files with this protocol when it is in the protected mode. It is recommended to leave this protocol in the protected mode to increase the security of Windows.
If you enable this policy setting the protocol is fully Turn-Ond, allowing the opening of folders and files.
If you disable this rule setting the protocol is in the protected mode, allowing applications to only open a limited set of folders.
If you do not configure this policy setting the protocol is in the protected mode, allowing applications to only open a limited set of folders.
11.) Show hibernate in the power options menu
Shows or hides hibernate from the power options menu.
If you enable this rule setting, the hibernate option will be shown in the Power Options menu (as long as it is supported by the machine's hardware).
If you disable this rule setting, the hibernate option will never be shown in the Power Options menu.
If you do not configure this policy setting, users account will be able to choose whether they want hibernate to show through the Power Options Control Panel.
12.) Show lock in the user tile menu
Shows or hides lock from the user tile menu.
If you Turn-On this rule setting, the lock option will be shown in the User Tile menu.
If you disable this policy setting, the lock option will never be shown in the User Tile menu.
If you do not configure this rule setting, users account will be able to choose whether they want lock to show through the Power Options Control Panel.
13.) Show sleep in the power options menu
Shows or hides sleep from the power options menu.
If you enable this rule setting, the sleep option will be shown in the Power Options menu (as long as it is supported by the machine's hardware).
If you disable this policy setting, the sleep option will never be shown in the Power Options menu.
If you do not configure this rule setting, users account will be able to choose whether they want sleep to show through the Power Options Control Panel.
14.) Set a support web page link
Sets the target of the More Information link that will be displayed when the user attempts to start or run a program that is blocked by policy.
15.) Do not reinitialize a pre-existing roamed user profile when it is loaded on a machine for the first time
This policy setting allows administrators who have configured roaming profile in conjunction with Delete Cached Roaming Profile Group rule setting to ensure that FIle-Explorer will not reinitialize default program associations and other settings to default values.
If you Turn-On this policy setting on a machine that does not contain all programs installed in the same manner as it was on the machine on which the user had last logged on, unexpected behavior could occur.
16.) Turn off Data Execution Prevention for FIle-Explorer
Turn Off data execution prevention can authorize certain legacy plug-in applications to function without terminating FIle-Explorer.17.) Turn off heap termination on corruption
Disabling heap termination on corruption can allow certain legacy plug-in applications to function without terminating FIle-Explorer immediately, although FIle-Explorer may still terminate unexpectedly later.